What is SSH & SSH Key?

The Secure Shell (SSH) protocol sets up encrypted connections for remote logins and file transfers between computers.
SSH
SSH (Secure Shell) is a network protocol used to securely access and manage devices over a network.
When we say “SSH“ we often refer to software implementations that use this protocol for secure communication (like OpenSSH)
History
If we want to explain some history of ssh it goes like this :
The “Secure Shell protocol” was originally developed by Tatu Ylonen in 1995 in response to a hacking incident in some Finnish universities network.
A password sniffer had been installed on a server connected directly to the backbone, and when it was discovered, it had thousands of usernames and passwords in its database, including several from Ylonen's company.
That incident triggered Ylonen to study cryptography and develop a solution he could use himself for remote login over the Internet safely.
Telnet protocol was commonly used before SSH for remote access, but it lacks encryption, making it so much less secure.
In short, the ssh that is currently used for almost all datacenters in the world is the result of these events.
How this thing work in nutshell
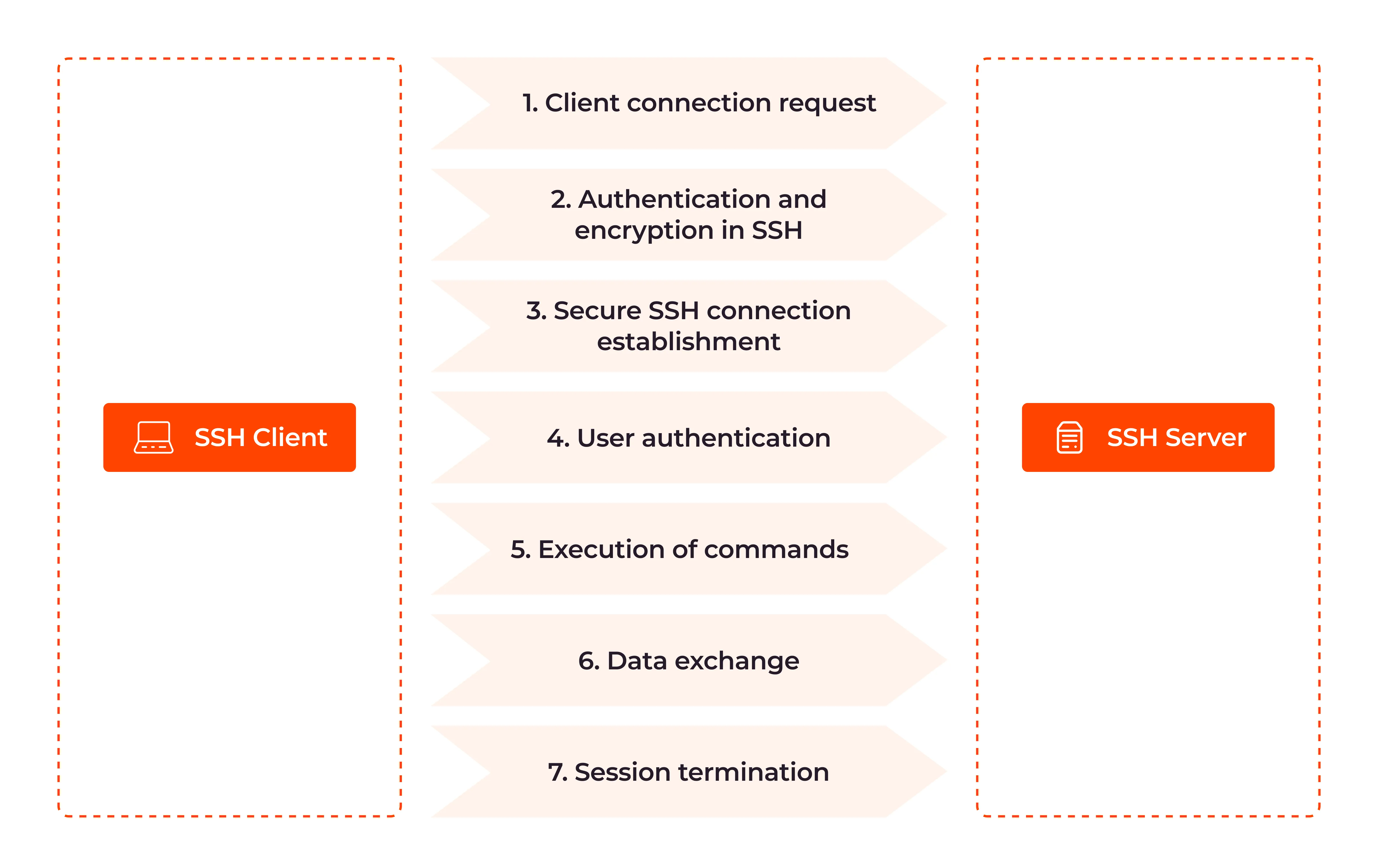
The protocol works in the client-server model, which means that the connection is established by the SSH client connecting to the SSH server. The SSH client drives the connection setup process and uses public key cryptography to verify the identity of the SSH server. After the setup phase the SSH protocol uses strong symmetric encryption and hashing algorithms to ensure the privacy and integrity of the data that is exchanged between the client and server.
The figure below presents a simplified setup flow of a secure shell connection
SSH Keys
So when you access another computer or server, you probably use a password. we use passwords all the time in lots of websites and etc. But from a security or comfort prospective they are often horrible.
For most of you, your password probably contain ‘1234‘ or ‘123456‘ Or in the vice versa, your password is probably god! as if you can not memorize it. You often end up with copy pasting. it quickly become tedious. So what is the solution?
Yes! SSH Keys!
An SSH key is an access credential in the SSH protocol. Its function is similar to that of user names and passwords, but the keys are primarily used for automated processes & for simplifying the process of logging into a server without the need to enter a password each time.
Auth types
SSH supports several authentication methods.
Two of most popular ones are
- Password Auth
- Public key Auth ( often refereed to as SSH keys )
in the Password method, it uses the user’s password for logging in. (your actual user in operating system )
in the Public key Auth, it involves a pair of cryptographic (a private key and a public key). The public key is stored on the server, and the private key stored on the user computer.
Next
In this post i just wanted to explain ssh and ssh keys in short terms. in the next posts, i will explain more about how we can exactly run ssh (+ configuring ssh keys) on our server.
As Always, thank you for taking your time and reading this post.